Unified threat management for scalable security operations

Endpoint Threat Analytics
Elevate your security strategy with our Endpoint Threat Analysis (ETA). Real-time monitoring of your device activities gives you the ability to detect and mitigate threats at their inception, enhancing your network’s resilience.
Overview of ETA
68% of organizations have experienced one or more endpoint attacks that successfully compromised data and/or their IT infrastructure. Utilizing ArmorPoint’s ETA will detect hidden threats, assess vulnerability impact, and strengthen defense strategies to enhance business resilience.
- Unrestricted Visibility: Gain complete visibility into your network’s endpoint activities
- Understand Application Risks: Identify potential vulnerabilities within your applications
- Real-time Threat Detection: Proactively identify threats as they emerge
Deep System Visibility
Receive in-depth insights into your system’s daily activities and behaviors. ArmorPoint’s ETA allows you to precisely understand and monitor system operations while swiftly detecting any unusual or anomalous activities.

Application Vulnerability Reporting
Stay fully informed about the vulnerabilities in your applications with detailed reporting. ArmorPoint’s ETA provides comprehensive information on application weaknesses, empowering you to take proactive measures to secure your systems effectively.
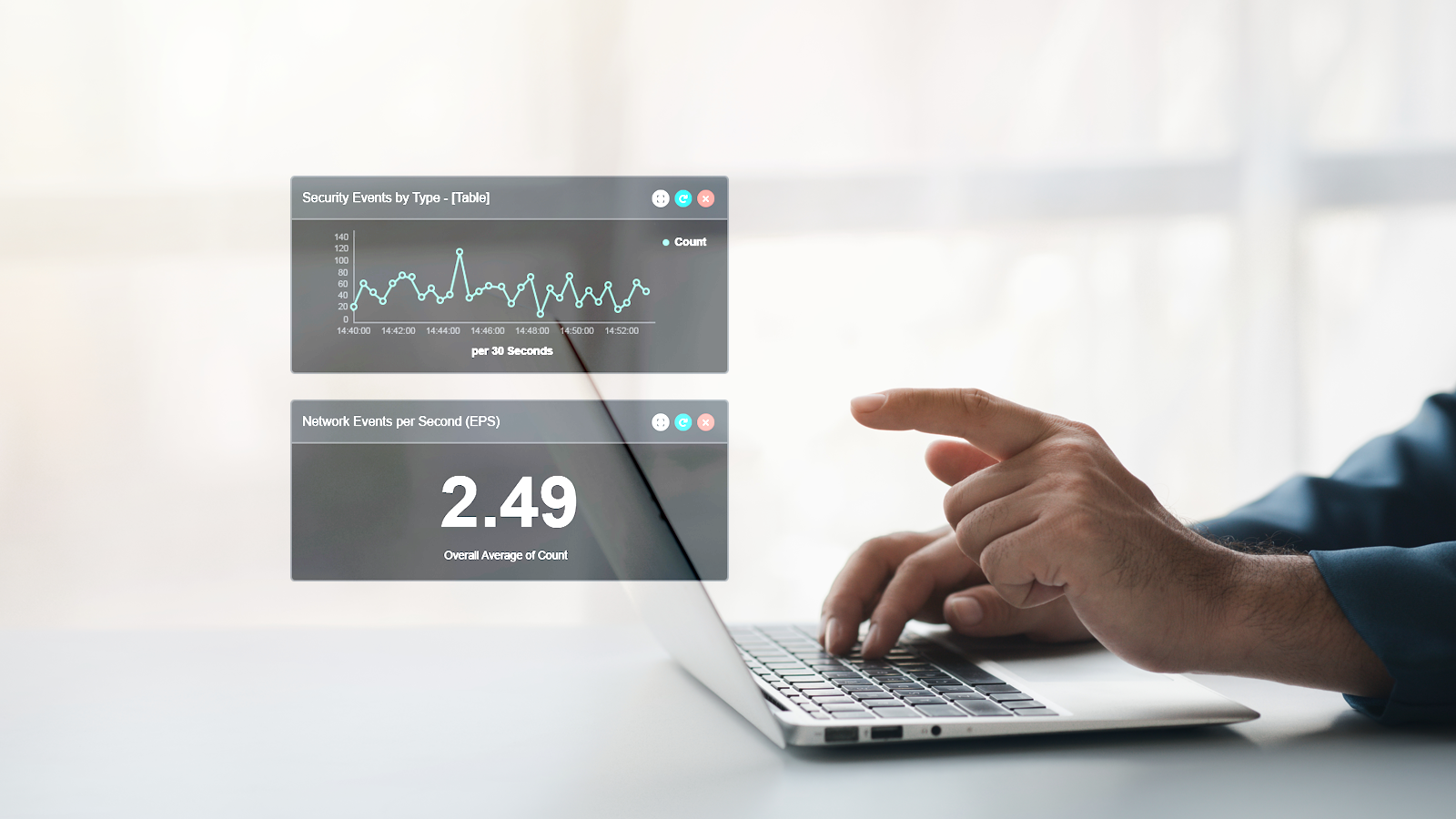
Advanced Threat Detection
Protect your endpoints with confidence using ArmorPoint’s ETA. Our advanced threat detection capabilities continuously monitor your systems, identifying and mitigating emerging threats in real-time.
Integrations
How It Works
ArmorPoint’s Endpoint Threat Analytics offers a strategic approach to enhancing your cybersecurity, focusing on comprehensive system, user, and identity insights.

Meet With Our Experts
Schedule a demo with our team to explore how our Endpoint Threat Analytics can enhance your security.

Implement Endpoint Threat Analytics
Deploy our solutions for robust visibility into system processes, user activities, and identity verifications, ensuring comprehensive threat detection.

Encrypted Data Processes
Strengthen your cybersecurity posture with advanced insights into system and user behavior, building a resilient defense against evolving threats.

Testimonial
“ArmorPoint has made it so I can sleep in on the weekends.”
– Carl Lawrence, Partner/Executive Vice President, Management Resource Group





More from ArmorPoint’s Managed SOC
Consolidate disparate data generated from your existing EDR tool
Next-gen endpoint threat detection and remediation

Request a Demo
Get a behind the scenes look at our robust security platform.